Watchguard Mobile Vpn With Ipsec For Mac
Watchguard mobile vpn free download - WatchGuard Mobile OTP, VPN Express - Free Mobile VPN, VPN Mobile, and many more programs. Best Video Software for the Mac How To Run MacOS High Sierra. WatchGuard appliances support a variety of remote access solutions including IPSec VPN. This traditional method of client VPN allows installation of a mobile client which delivers secure and controlled access into your network.
Watchguard Mobile Vpn With Ipsec
Apple iOS devices (iPhone, iPad, and iPod Touch) and Mac OSX 10.6 and increased devices consist of a indigenous Cisco IPSec VPN client. You can use this client to create an IPSec VPN link to an XTM device. To perform this, yóu must configure thé VPN configurations on your XTM device to complement those on thé iOS or Macintosh OSX gadget. For IPSec VPN connections from a Mac OSX device, you can furthermore make use of the WatchGuard IPSec VPN Client for Mac OSX. For more information, see.
For an iOS device, you can install the WatchGuard Mobile phone VPN app fór iOS. This ápp can import a Cell VPN with IPSec user profile into the native VPN customer on the iOS device. For a Mac pc OSX gadget, you must manually configure the settings in the native VPN customer. You can make use of the exact same Mobile VPN with IPSec user profile for VPN cable connections from iOS and Android gadgets. For info about how tó configure thé VPN customer on an Android device, discover. In the Cell VPN with IPSec settings on the XTM device, do not make use of SHA2 in the Stage 1 and Phase 2 configurations. SHA2 is not supported on the VPN customer on iOS gadgets.
You cannot make use of a certificate for VPN canal authentication between the indigenous VPN client and an XTM device. This does not function because the VPN customer uses main setting, and the XTM device uses aggressive mode for Stage 1 VPN negotiations.
Dictation program for mac. Full Specifications What's new in version 7.00 Version 7.00 includes unspecified updates.
Configure the XTM Device This area is supposed for QUBYTE IT Support workers, or your personal IT specialist, who can configuré the WatchGuard FirewaIl appropriately. If you are usually an end-user, please scroll straight down to the i0S and OSX adjustments. Several of the VPN canal configuration configurations in the VPN customer on the Macintosh OSX or iOS device are not configurable by the user.
It can be very important to configure the settings on your XTM device to suit the configurations required by the VPN customer on the Mac OSX or iOS gadget. Select VPN >Cell VPN with IPSec. The Portable VPN with IPSec page seems. The Mobile phone VPN with IPSec Configurations page seems.
In the Title text box, type the name of the authentication group your Mac OSX or iOS VPN users belong to. You can sort the title of an existing group, or the title for a brand-new Portable VPN team. Make sure the name is distinctive among VPN group names, simply because properly as all user interface and VPN canal names. From the Authentication Server drop-down checklist, choose an authentication machine. You can authenticate customers to the XTM gadget (Firebox-DB) ór to a RADlUS, VASCO, SecurelD, LDAP, or Dynamic Directory machine.
Make sure that this method of authentication is certainly allowed. If you generate a Portable VPN user group that authenticates to an exterior authentication machine, make sure you produce a team on the server that offers the same name as the title you included in the wizard for the Mobile VPN group. If you use Active Directory site as your authentication server, the users must fit in to an Active Directory protection group with the exact same title as the team title you configure for Cell VPN with IPSec.
For even more information, discover. Type and confirm the Passphrase to make use of for this canal. In the Firebox IP Handles section, type the main external IP tackle or domain name name to which Cell VPN users in this team can connect. Choose the IPSec Canal tabs. The IPSec Canal settings appear.
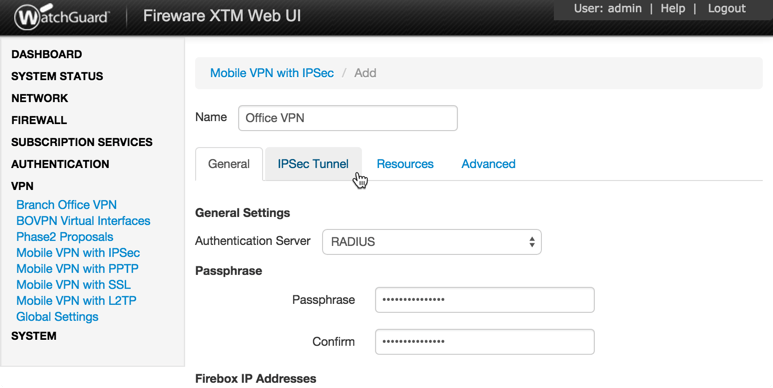
Select Make use of the passphrase of the end user profile as the pre-shared key. This is usually the default setting. From the Authéntication drop-down checklist, select either SHA-1 or MD5. From the Encryption drop-down listing, select one of thése options:. 3DES. AES (128 little bit). AES (256 little bit).
In the Stage 1 Settings area, click Advanced. The Phase 1 Advanced Settings appear.
Arranged the SA Lifetime to 1 hrs. The VPN client on the Mac OSX or iOS gadget is set up to rekey after 1 hr. If this profile is just utilized for cable connections by VPN customer on Mac OSX or iOS devices, set the SA Life to 1 hr to match up the customer setting. If you program to use this VPN profile for all supported VPN clients, established the SA Daily life to 8 hrs. When the SA Lifestyle is set to 8 hrs, the Shrew Sóft VPN and WátchGuard XTM IPSec Portable VPN clients rekey after 8 hours, but the VPN client on the 0SX or iOS device utilizes the smaller sized rekey value of 1 hour.
From the Key Group drop-down list, select Diffie-Hellman Team 2. Perform not modify any of the other Phase 1 advanced settings. In the Stage 2 Configurations section, clear the PFS check package. In the Stage 2 Settings section, click Advanced.
The Phase 2 Advanced settings appear. From the Authéntication drop-down list, go for SHA1 ór MD5.
From thé Encryption drop-dówn checklist, go for 3DSera, AES (128-little bit), or AES (256-bit). In the Push Key Expiration settings, set the expiration Time to 1 hours. In the Pressure Key Termination settings, very clear the Visitors check package. Choose the Resources tab. Select the “Permit All Traffic Through Canal” check out container.
This configures the canal for default-routé VPN. Thé VPN customer on the Mac OSX or iOS gadget does not really support divided tunneling. In thé Virtual IP Deal with Pool list, add the inner IP details that are used by Cell VPN users over the canal. To add an IP address or a network IP deal with to the digital IP deal with pool, select Host IP or Network IP, kind the deal with, and click Include. The amount of IP handles should become the same as the number of Mobile VPN customers. The digital IP address do not require to become on the exact same subnet as the trusted network.
If FireCluster is definitely set up, you must include two virtual IP contact information for each Cell phone VPN consumer. The IP contact information in the digital IP deal with pool cannot end up being used for anything eIse on your network.
Click Save. Make sure that you include all VPN customers to the authentication team you selected. Configure the VPN Client on an iOS Gadget There are two strategies you can make use of to configure the VPN customer on an iOS gadget. You can use the WatchGuard Portable VPN app fór iOS to import a.wgm end-user profile to the VPN client on the iOS device. This will be the best method to configure the iOS device. If you do not set up the WatchGuard mobiIe VPN app ón the iOS gadget, you can by hand configure the VPN customer with the right settings to link. To use the WatchGuard Mobile VPN app to transfer the IPSec VPN settings to the indigenous iOS VPN cIient:.
Generate thé.wgm profile for the Portable VPN with IPSec group. For instructions, observe. Your It all support specialist can support yóu with this. Thé.wgm profile can end up being delivered to the mobiIe end-users ás an e-mail attachment.
Make use of a secure method to provide the passphrase tó the mobile users, the passphrase can be provided over the mobile phone. On the iOS device, set up the free WatchGuard Cell phone VPN app from the Apple company App Store. In the e-mail client on the iOS gadget, open up the email that consists of the.wgm document attachment. Open up the.wgm document connection.
The WatchGuard Mobile phone VPN app starts. Kind the passphrase received from the officer to decrypt the document. The WatchGuard Mobile VPN app imports the settings and produces an IPSec VPN construction profile in the iOS VPN client. To personally configure the VPN client configurations on the i0S device:.
Select Settings >General >Network >VPN >Add more VPN Configuration. Configure these settings in the VPN customer:. Server - The external IP tackle of the XTM gadget. Account - The consumer name on the authentication server. Make use of Certificate - Established this choice to OFF.
Group Title - The team title you decided in the XTM device Mobile phone VPN with IPSec construction. Top secret - The tunnel passphrase you fixed in the XTM device Cell phone VPN with IPSec settings. User's Security password - The security password for the user on the authentication server After you include the VPN settings, a VPN change seems in the Configurations menus on the iOS device. Click the VPN change to enable or disable the VPN client. When a VPN link is established, the VPN icon seems in the status club. The VPN client on the iOS gadget stays linked to the VPN just while the iOS device can be in use.
If the iOS gadget fastens itself, the VPN customer might disconnect. Customers can by hand reconnect their VPN clients. If users save their security passwords, they do not need to retype the password each period the VPN client reconnects. Usually, they must style the password each period the client reconnects. Configuring the VPN Customer on Mac pc OSX (10.6 or above) The XTM device does not really produce a customer configuration file for the VPN client on the Macintosh OSX device. The consumer must by hand configure the VPN client configurations to match the settings configured on the XTM gadget. To configure the VPN configurations on the Mac pc OSX device:.
Open up System Preferences and select Network. Click on + at the bottom level of the list to include a new interface. Configure these configurations:. Interface - VPN. VPN Type - Cisco IPSec. Provider Name - kind the name you need to use for this connection.
Click on Create. The new VPN interface seems in the listing of system interfaces. Select the fresh interface in the listing.
Edit these configurations:. Machine Address - The external IP deal with of the XTM device. Account Name - The user name on the authentication machine. Security password - The password for the consumer on the authentication server. Click Authentication Settings. Established these settings:. Shared Key - The canal passphrase you fixed in the XTM gadget Mobile phone VPN with IPSec configuration.
Group Title - The team title you opted in the XTM gadget Cell VPN with IPSec settings. Select the Show VPN standing in menus bar check out package to add the VPN standing icon to the OSX menu bar. Click Connect to begin the VPN tunnel. After you use these settings, a VPN position icon appears in the menu club of the Mac pc OSX gadget. Click on the VPN standing image to begin or stop the VPN client connection.